Five-year-old program provides government with direct access to email, messages, browser history, more
The US National Security
Agency and Federal Bureau of Investigation have been harvesting data
such as audio, video, photographs, emails, and documents from the
internal servers of nine major technology companies, according to a
leaked 41-slide security presentation obtained by The Washington Post and The Guardian. According to The Washington Post,
the program's slides were provided by a "career intelligence officer"
that had "firsthand experience with these systems, and horror at their
capabilities," and wished to expose the programs "gross intrusion on
privacy."
The program, codenamed PRISM,
is considered highly classified and has never been made public before.
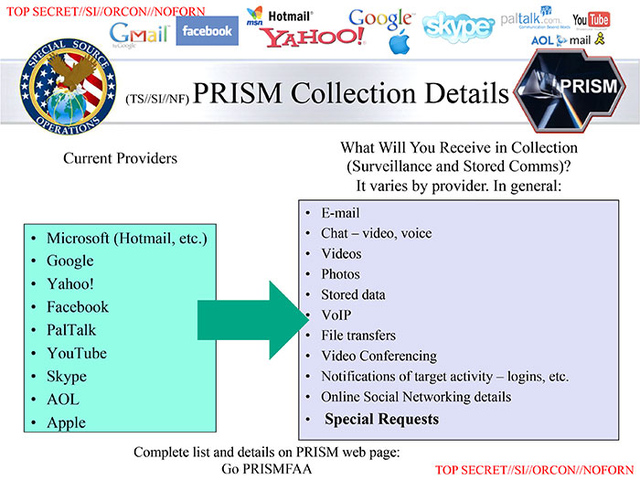
The list of companies involved are the who's who of Silicon Valley:
Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, and
Apple. Dropbox, though not yet an official part of the program, is said
to be joining it soon. These companies have all willingly participated
in the program, says the Post.
According to the leaked
presentation, the program has been in action since 2007, and is
considered the biggest contributor to the daily briefings given to the
President, providing data in 1,477 articles last year alone. Allegedly,
nearly one in seven intelligence reports from the NSA contains data from
the PRISM program. The NSA has the ability to pull any sort of data it
likes from these companies, but it claims that it does not try to
collect it all. The PRISM program goes above and beyond the existing
laws that state companies must comply with government requests for data,
as it gives the NSA direct access to each company's servers —
essentially letting the NSA do as it pleases. The program was initiated
to overcome what the NSA saw as constraints within the existing FISA
warrant program that did not allow the agency to make us of the
"home-field advantage" provided by having most of the internet's biggest
companies on US soil.
The who's who of Silicon Valley are involved in the NSA's PRISM program.
Microsoft was the first company
to bow to the government's wishes and join the PRISM program in 2007,
while Apple held out for five years before agreeing. Though Google and
Facebook are a part of PRISM, Twitter has not yet joined. Apparently,
the only members of Congress that knew about PRISM's existence were
bound by oath not to speak of it publicly. In a statement provided to
both The Washington Post and The Guardian, Google denied that the government had any sort of backdoor access to its systems:
"Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'backdoor' into our systems, but Google does not have a 'backdoor' for the government to access private user data."
The training documents for the
program reveal that the NSA collects a large amount of data on the
American public through the PRISM program. For example, if a specific
target is investigated using PRISM, that target's complete inbox and
outbox is swept, in addition to anyone that is connected to it. This
high-level of access was initially given to the NSA by President Bush
and was later renewed in 2012 by President Obama.
This report follows the news from earlier this week of the NSA's involvement in collecting call data and records from Verizon in another massive surveillance partnership.
Update: The Director of National Intelligence issued a statement today,
aiming to clear up "inaccuracies" in reporting on the PRISM program.
The DNI argues that only people outside of the United States have been
targeted, and that the program “does not allow” the targeting of
citizens or others within US borders. “This program was recently reauthorized by Congress
after extensive hearings and debate,” said the official, adding that,
“information collected under this program is among the most important
and valuable intelligence information we collect, and is used to protect
our nation from a wide variety of threats.”
The word “target” takes on special significance given what has been reported by former NSA codebreaker William Binney
and others. The Stellar Wind program, for which Binney claims to have
contributed much of the base code, is said to compile massive amounts of
internet traffic, which can then be queried at a later time. According
to USSID 18, a top-secret NSA manual of definitions and legal
directives, an “intercept” only occurs when the database is queried —
when someone actually reads the text on a screen.


No comments:
Post a Comment